
The sudden dominance of first-person view drones and loitering munitions on the modern battlefield has forced a radical rethink of how armored vehicles must be defended against low-cost aerial threats. Traditional active protection systems, while effective against high-velocity anti-tank missiles,
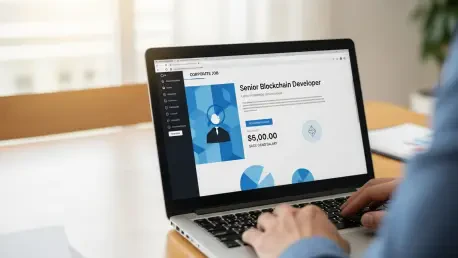
A sophisticated global campaign orchestrated by state-sponsored North Korean hackers is actively exploiting the trust inherent in the professional recruitment process to infiltrate the technology sector. The notorious Lazarus Group stands at the forefront of this effort, masterfully creating the
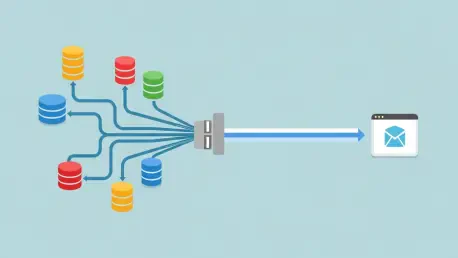
The modern enterprise data landscape is a sprawling, complex ecosystem where monolithic relational databases now share the stage with a diverse cast of NoSQL solutions, creating a fragmented and challenging environment for developers. This reality has catalyzed a strategic shift toward unified data
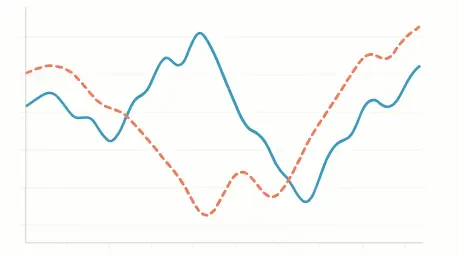
While the principle of randomization stands as the undisputed cornerstone of modern A/B testing, a subtle yet potent threat can systematically dismantle the integrity of an experiment long after users have been neatly sorted into control and treatment groups. This insidious problem, known as

Scientists at Washington State University are at the forefront of addressing one of the most critical paradoxes of our time, exploring the dual role of Artificial Intelligence in shaping the nation’s energy grid and cybersecurity framework. AI is simultaneously a source of immense strain on these

The Linux desktop ecosystem, long celebrated for its flexibility and power, is confronting a profound and deeply rooted deficiency that jeopardizes its relevance in an era defined by user security and seamless authentication. This critical flaw—the absence of a secure, unified, and modern
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27