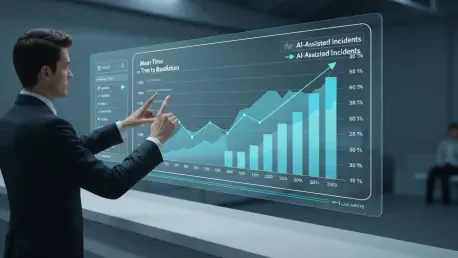
For years, the concept of a SOC copilot—an AI assistant that could instantly parse security data and slash response times—has been the ultimate dream for security teams. Yet, as generative AI has become a reality, so has the potential for that dream to become a security nightmare. We sat down with

In today's fast-paced world of cloud-native development, security can no longer be an afterthought. We're joined by our SaaS and Software expert, Vijay Raina, a specialist in enterprise technology who has been at the forefront of rethinking how we build secure systems. With applications being

The seismic mergers and acquisitions that defined the cybersecurity landscape in 2025 were far more than just financial maneuvers; they represented a fundamental and strategic realignment of the entire digital defense industry. This wave of consolidation was a direct and calculated response to a

With data from the Global Anti-Scam Alliance revealing that a staggering 73% of Malaysian citizens have been targeted by scam attempts, the nation faces one of the highest rates of digital fraud in Southeast Asia. This pervasive threat has prompted a groundbreaking response from the

The inherent risks and complex legal landscape of the equine industry present a persistent challenge for professionals who dedicate their lives to working with horses. A new initiative based in Saluda, North Carolina, aims to directly address these concerns by creating a more secure and
The rapid integration of artificial intelligence into business operations has unveiled a startling vulnerability, with recent data showing an overwhelming 99% of organizations have experienced at least one attack on their AI systems in the last year. This alarming statistic, however, does not point