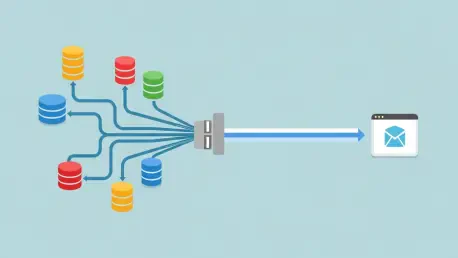
The modern enterprise data landscape is a sprawling, complex ecosystem where monolithic relational databases now share the stage with a diverse cast of NoSQL solutions, creating a fragmented and challenging environment for developers. This reality has catalyzed a strategic shift toward unified data
While the principle of randomization stands as the undisputed cornerstone of modern A/B testing, a subtle yet potent threat can systematically dismantle the integrity of an experiment long after users have been neatly sorted into control and treatment groups. This insidious problem, known as

Scientists at Washington State University are at the forefront of addressing one of the most critical paradoxes of our time, exploring the dual role of Artificial Intelligence in shaping the nation’s energy grid and cybersecurity framework. AI is simultaneously a source of immense strain on these

The escalating sophistication of cyber threats has created a critical global challenge, far outstripping the available supply of skilled professionals capable of mounting an effective defense. This widening talent chasm places unprecedented pressure on both public and private sector organizations,

The proliferation of smart devices has seamlessly integrated the Internet of Things into the fabric of daily life, yet the security measures protecting this interconnected web have failed to evolve at the same pace. This disparity has created a dangerous landscape where the simple, traditional

In an automotive landscape where the in-car experience is increasingly defined by software, Geely has rolled out a significant over-the-air update for its EX5 electric SUV, addressing key user feedback and enhancing the vehicle’s day-to-day usability. This latest software push is centered on