
In an automotive landscape where the in-car experience is increasingly defined by software, Geely has rolled out a significant over-the-air update for its EX5 electric SUV, addressing key user feedback and enhancing the vehicle’s day-to-day usability. This latest software push is centered on

The proliferation of passwordless authentication through passkeys represents a monumental shift towards a more secure and user-friendly digital world, but this evolution has largely been confined to devices with conventional screens. For the rapidly expanding ecosystem of screenless or

In the landscape of higher education, the rapid and reliable dissemination of information during a crisis is not just a logistical challenge but a fundamental component of institutional responsibility. Virginia Tech is actively reinforcing this commitment with a comprehensive, university-wide test
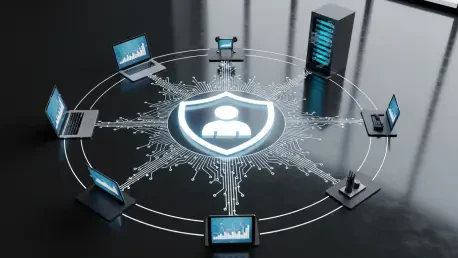
The landscape of enterprise cybersecurity is undergoing a radical and irreversible transformation, moving beyond the familiar but failing metaphor of a fortified castle. For decades, security was synonymous with a strong network perimeter—a digital wall built with firewalls and VPNs designed to

The green checkmark on the status page offers a comforting illusion of stability, but behind the scenes, the human operators propping up that facade are often just one complex outage away from burnout and catastrophic failure. In the world of Site Reliability Engineering (SRE), the relentless

Indian Railways, one of the world's most extensive and heavily used rail networks, has embarked on an ambitious and critically important mission to revolutionize its safety infrastructure with the rapid deployment of its indigenous automatic train protection system. On January 30, 2026, the