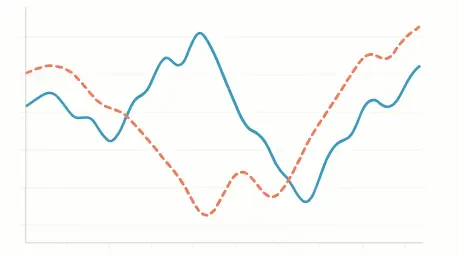
While the principle of randomization stands as the undisputed cornerstone of modern A/B testing, a subtle yet potent threat can systematically dismantle the integrity of an experiment long after users have been neatly sorted into control and treatment groups. This insidious problem, known as
Transforming a deployment from a tense, fingers-crossed moment into a predictable, automated verification process is the hallmark of a mature DevOps culture. The decision of how to integrate quality assurance into a release pipeline is not just a technical choice; it shapes the speed, reliability,

The silent, stomach-churning anxiety that permeates an engineering team's communication channels on deployment day is a universal symptom of a multi-million-dollar problem plaguing the software industry. Despite years of progress with DevOps methodologies and sophisticated CI/CD pipelines, a

In the landscape of higher education, the rapid and reliable dissemination of information during a crisis is not just a logistical challenge but a fundamental component of institutional responsibility. Virginia Tech is actively reinforcing this commitment with a comprehensive, university-wide test

The green checkmark on the status page offers a comforting illusion of stability, but behind the scenes, the human operators propping up that facade are often just one complex outage away from burnout and catastrophic failure. In the world of Site Reliability Engineering (SRE), the relentless

The relentless acceleration of software development, fueled partly by the very artificial intelligence designed to assist it, has created a critical imbalance where traditional security practices can no longer keep pace with the sheer volume of code production. This review explores the evolution of
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25