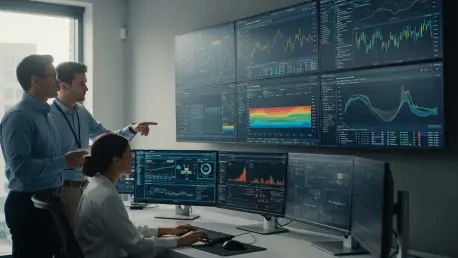
The familiar story of a rapidly growing Software-as-a-Service company often reaches a frustrating climax where spiraling infrastructure costs fail to deliver the expected gains in performance, leaving both engineers and customers bewildered. This common scenario highlights a fundamental
The recurring thirty-minute delay caused by a simple Terraform pipeline failure represents one of the most persistent and costly interruptions in modern software development, directly impacting project timelines and engineering morale. This research summary outlines a proof-of-concept system that

When it comes to migrating large, mission-critical systems to the cloud, the term "lift-and-shift" can be deceptively simple. While the tools for moving virtual machines have matured, the underlying physics of a distributed cloud environment introduces complexities that can derail even the most
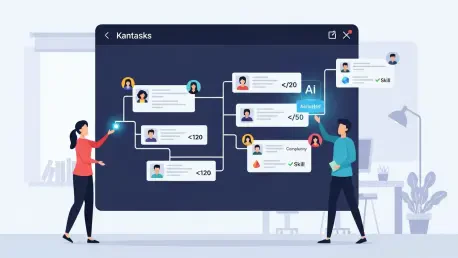
The rapid evolution of software engineering, once driven by the internet and cloud computing, is now being supercharged by artificial intelligence, dramatically shortening the path from a minimum viable product to a robust, large-scale system. Tasks that previously consumed days of collaborative

The cumbersome and often lengthy process of conducting fingerprint-based background checks, a critical step for employment and licensing in numerous sectors, is poised for a significant transformation in Utah. An announcement on January 22, 2026, confirmed that the Utah Department of Public Safety
Our SaaS and Software expert, Vijay Raina, is a specialist in enterprise SaaS technology and tools. He also provides thought-leadership in software design and architecture. In our conversation, we explored the evolution of Security Operations Centers (SOCs), delving into how AI is not just a