
The realm of software development is experiencing a profound transformation, driven by the rapid integration of artificial intelligence (AI) into every facet of the industry, fundamentally altering how applications are conceived, coded, and rolled out. No longer confined to theoretical discussions

In an era where software development races ahead at breakneck speed, the security practices meant to safeguard these innovations often struggle to keep pace, creating a precarious landscape for organizations worldwide. A recent comprehensive report surveying over 1,000 global professionals reveals

In the ever-evolving landscape of cloud computing, managing storage costs while maintaining accessibility remains a critical challenge for organizations of all sizes. Amazon Web Services (AWS) offers a robust solution through its S3 storage service, featuring tools like Intelligent-Tiering and

What happens when a startup team, racing against tight deadlines, discovers that their own tools are slowing them down? In a world where every second counts toward launching the next big feature, a small development squad stumbled upon a game-changing realization: their Continuous Integration and
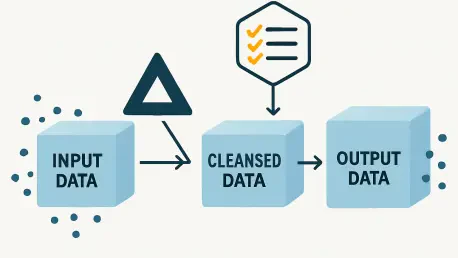
I'm thrilled to sit down with Vijay Raina, a renowned expert in enterprise SaaS technology and software architecture. With his deep knowledge of modern data systems and thought leadership in design, Vijay is the perfect person to guide us through the intricacies of data quality management,

In the ever-evolving landscape of software development, countless organizations embark on the journey of adopting microservices with the tantalizing promise of agility, scalability, and team independence, only to stumble into an unexpected quagmire known as distributed monoliths. These systems,