
The adoption of sophisticated data management features like liquid clustering often comes with the high expectation of seamless performance gains, yet many engineering teams find their most critical MERGE operations slowing to a crawl instead of accelerating. This disconnect between a feature's
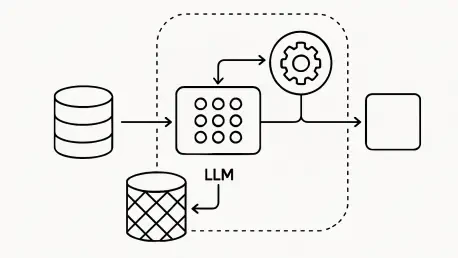
The most consequential conversations happening in boardrooms and engineering pods today are no longer about which large language model to choose, but about the sophisticated architectural frameworks required to make them truly work for the enterprise. As these powerful models move from isolated

Navigating the complex maze of enterprise networks, with their layers of proxies, firewalls, and VPNs, often feels like sending data through a storm where connection timeouts and packet loss are the norm. In this unpredictable environment, building a resilient frontend application is not just a
In the intricate world of large-scale data processing, the most formidable obstacle often emerges not during complex model training but in the seemingly straightforward task of writing the final output to storage. The journey of transforming raw data into actionable insights can abruptly halt at

The persistent gap between detecting a system failure and resolving it exposes a fundamental flaw in modern operations, where sophisticated observability tools generate alerts faster than human teams can coherently respond. This guide provides a strategic blueprint for closing that gap by shifting

The digital signage industry has long navigated a challenging divide between low-cost, feature-limited consumer devices and powerful, yet prohibitively expensive, professional-grade media players. This gap often forced small businesses, schools, and even larger enterprises to compromise, choosing