
In an era where cyber threats are becoming increasingly sophisticated, leveraging artificial intelligence to both attack and defend digital infrastructures, Databricks has stepped forward with a transformative solution that promises to reshape the landscape of organizational security. As a leader

In an era where technology permeates every facet of daily life, from personal communications to critical infrastructure, the integrity of software systems stands as a cornerstone of safety and stability, and its vulnerabilities can have far-reaching consequences. At the recent Cyber Security Week

In an era where software development races ahead at breakneck speed, the security practices meant to safeguard these innovations often struggle to keep pace, creating a precarious landscape for organizations worldwide. A recent comprehensive report surveying over 1,000 global professionals reveals

In the ever-evolving landscape of cloud computing, managing storage costs while maintaining accessibility remains a critical challenge for organizations of all sizes. Amazon Web Services (AWS) offers a robust solution through its S3 storage service, featuring tools like Intelligent-Tiering and

In the ever-evolving landscape of software development, countless organizations embark on the journey of adopting microservices with the tantalizing promise of agility, scalability, and team independence, only to stumble into an unexpected quagmire known as distributed monoliths. These systems,
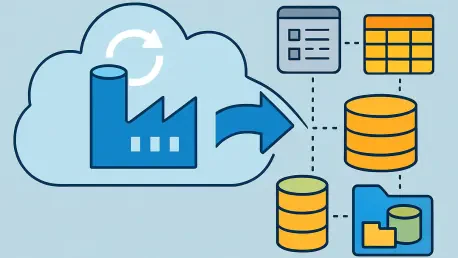
In today’s data-driven landscape, businesses face the daunting task of managing information from countless sources, often struggling to integrate disparate systems into a cohesive workflow, while the challenge of moving and transforming data across cloud and on-premises environments can stall even