
The mobile applications central to our daily lives don't suddenly break or fail; instead, they undergo a subtle yet relentless process of aging that eventually renders them obsolete. This perspective reframes an app's relevance not as a permanent achievement but as a finite lifecycle with a

The intricate web of digital services that defines modern life, from mobile banking to connected vehicles, is woven together by the silent, powerful work of Application Programming Interfaces (APIs). As organizations across every sector accelerate their digital transformation initiatives, the

An in-depth analysis of the global API Management Services Market reveals a sector on the brink of significant and sustained expansion, driven by fundamental shifts in how modern enterprises design and deploy their technology strategies. The market, currently valued at USD 3.72 billion, is

Connecting sophisticated AI applications to diverse, proprietary data sources has quickly become one of the most significant bottlenecks in modern software development, often leading to a complex web of brittle, custom-built integrations. This challenge underscores the critical need for a
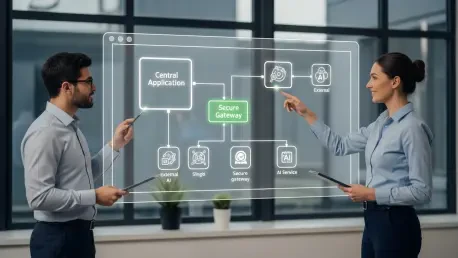
As a specialist in enterprise SaaS, I’ve seen firsthand how the integration of Large Language Models is revolutionizing software. However, moving from a fascinating demo to a secure, production-ready service is where the real challenge lies. Today, we're diving deep into the Model Context Protocol

The journey for an Indian software-as-a-service company from local success to global contender is often bottlenecked not by product quality but by the intractable complexities of international payment processing. Beyond Simple Transactions The New Imperative for Indian Businesses on the World Stage