

Imagine a scenario where a burgeoning e-commerce platform struggles to balance the need for dynamic, real-time functionality with the demand for a content-rich blog to drive organic traffic, often forcing businesses to split their online presence across multiple domains or servers. This dual

I'm thrilled to sit down with Vijay Raina, a renowned expert in enterprise SaaS technology and a thought leader in software design and architecture. With his deep understanding of developer tools and community dynamics, Vijay offers invaluable insights into the evolving landscape of platforms like

Imagine a world where sipping a beverage or choosing a snack could actively contribute to a healthier lifestyle, all through a seamless mobile experience that gamifies wellness. This innovative vision is becoming a reality with Suntory, a global leader in beverages and food products, stepping

In an era where digital infrastructure increasingly relies on APIs, the security of these critical components has become a pressing concern for organizations across industries. With APIs often serving as the primary gateway for data exchange in modern applications, they have also emerged as a

In an era where digital transformation is no longer a choice but a necessity for enterprises across the globe, the intersection of artificial intelligence and cloud computing has become the cornerstone of business innovation. Snowflake (SNOW), a trailblazer in cloud data analytics, has carved out a

Welcome to an exciting conversation about the future of precision positioning technology! Today, I’m thrilled to speak with Vijay Raina, a renowned expert in enterprise SaaS technology and software architecture. With his deep knowledge of innovative tools and systems design, Vijay is the perfect
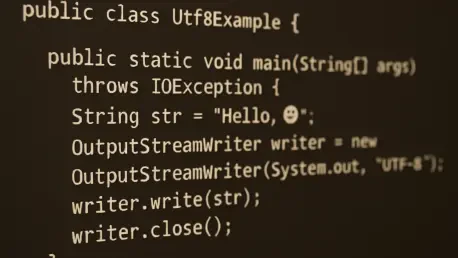
Have you ever poured hours into debugging a Java application only to discover that a simple encoding mismatch turned your data into gibberish across platforms? This frustrating scenario has plagued developers for decades, with text files misbehaving when moved between systems due to inconsistent

In an era where technology shapes nearly every aspect of daily life, the open source community stands as a cornerstone of innovation, driving solutions that are accessible, secure, and collaborative across the globe. This year, the Apache Software Foundation (ASF) hosts its flagship event,

In an era where software development is increasingly driven by speed and innovation, a groundbreaking approach known as vibe coding is capturing the attention of developers worldwide, promising to redefine the field. This method, powered by artificial intelligence and seamlessly integrated with

In an era where cybersecurity threats loom larger than ever, a recent disclosure by Cisco has sent shockwaves through the tech and security communities, highlighting a severe flaw in its Secure Firewall Management Center (FMC) software. Identified as CVE-2025-20265, this remote code execution (RCE)
ITCurated uses cookies to personalize your experience on our website. By continuing to use this site, you agree to our Cookie Policy